What is SecurITree?
Amenaza's SecurITree software enables analysts to make objective, risk-based security decisions regarding a system's threats. SecurITree's attack tree-based threat models analyze thousands of possible attacks against a defender's system. Each attack is assessed for feasibility by comparing each threat agent's capabilities with the resources they would require to execute the attack. Attacks are also evaluated to determine how well they satisfy an attacker's goals (thus providing an understanding of their degree of motivation). Attacks are assigned an estimate of probability based on the degree to which a given adversary finds them to be both feasible and desirable. Finally, each attack's likelihood is combined with the anticipated impact on the victim to yield an assessment of risk.
Once attacks with unacceptable levels of risk are identified, analysts can evaluate the effectiveness of proposed controls by adding the countermeasures to the threat models and observing the amount of risk reduction achieved.
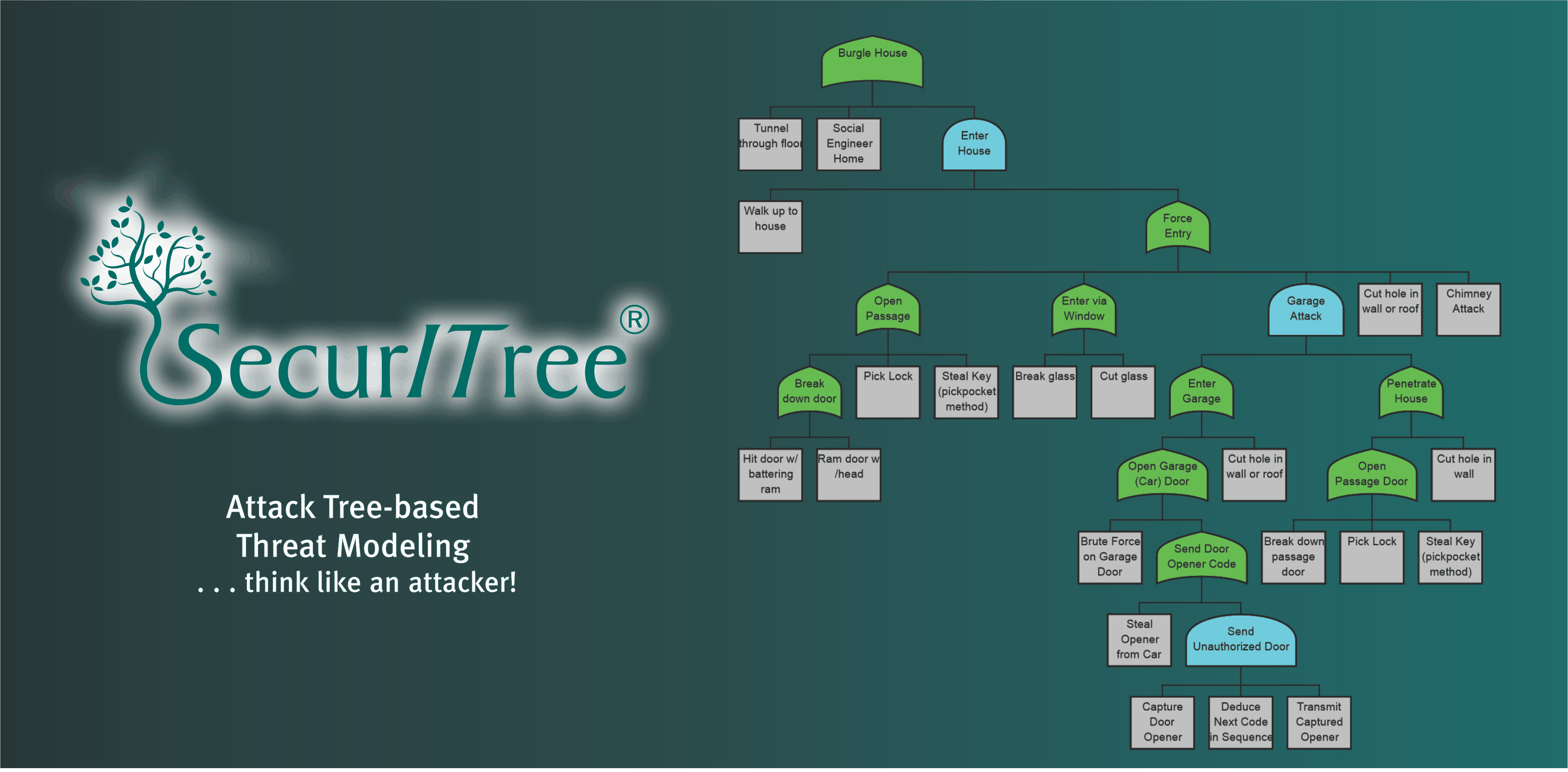
SecurITree is an easy to use software package for attack tree-based threat risk analysis . It runs on Windows-based PCs, Apple Mac-based workstations and Linux systems.
Although attack trees are conceptually quite simple, even in a small tree, the AND / OR tree logic can result in hundreds or thousands of paths that lead from the leaf nodes to the overall root objective. While trees can be sketched manually using paper and pencil, no human could explore all of the attack paths quickly and accurately - a software tool is required.
SecurITree makes it easy to create and populate attack trees. Nodes are created and linked together using SecurITree's graphical user interface. Parameters can be associated with tree nodes describing
- the resources an adversary would require to perform attack operations
- the benefits (and detriments) an adversary will obtain as they traverse nodes
- the negative impacts that the victim will suffer
SecurITree creates a list of every combination of leaf node events that forms a path leading to the root goal. Associated with each path, or attack scenario, is the set of resources, attacker benefits and victim impacts required to traverse the path.
Once the basic attack tree has been constructed, the analyst creates descriptions of the goals and capabilities of each possible adversary. These attacker descriptions are stored in threat agent profiles which can be used and reused in different analyses.
SecurITree quickly compares the characteristics of each attack scenario to each adversary's threat agent profile. The attack scenarios whose resource requirements and attacker benefits are a good fit with the characteristics of a particular threat agent profile are deemed to be highly probable. Attack scenarios whose combination of likelihood and victim impact are high are designated as high risk. The math behind all calculations is well documented - SecurITree does not use magic black boxes to pluck answers out of thin air.
If one or more attack scenarios have an unacceptable risk level the analyst can create variants of the model (called alternatives) to test the efficacy of controls and countermeasures. This makes it possible to perform cost-benefit analysis on security countermeasures.
Although SecurITree was primarily developed to analyze hostile threats, it can also deal with random, happenstance events (fault tree analysis) for which probability is known directly. A unique feature of SecurITree models is the ability to deal with scenarios involving both random and malicious activities. This is often the case for opportunistic adversaries, who take advantage of random events that make attacks easier or more attractive.
SecurITree's advanced analytic and reporting functions ensure that you can see the forest through the trees, and include the information in the documents you create for management.

