Amenaza Technologies delivers actionable strategy for critical infrastructure and enterprise security leaders. We go beyond surface-level vulnerability scans and compliance checklists — using attack trees to model real-world attack feasibility and quantifying business impact at the executive level.
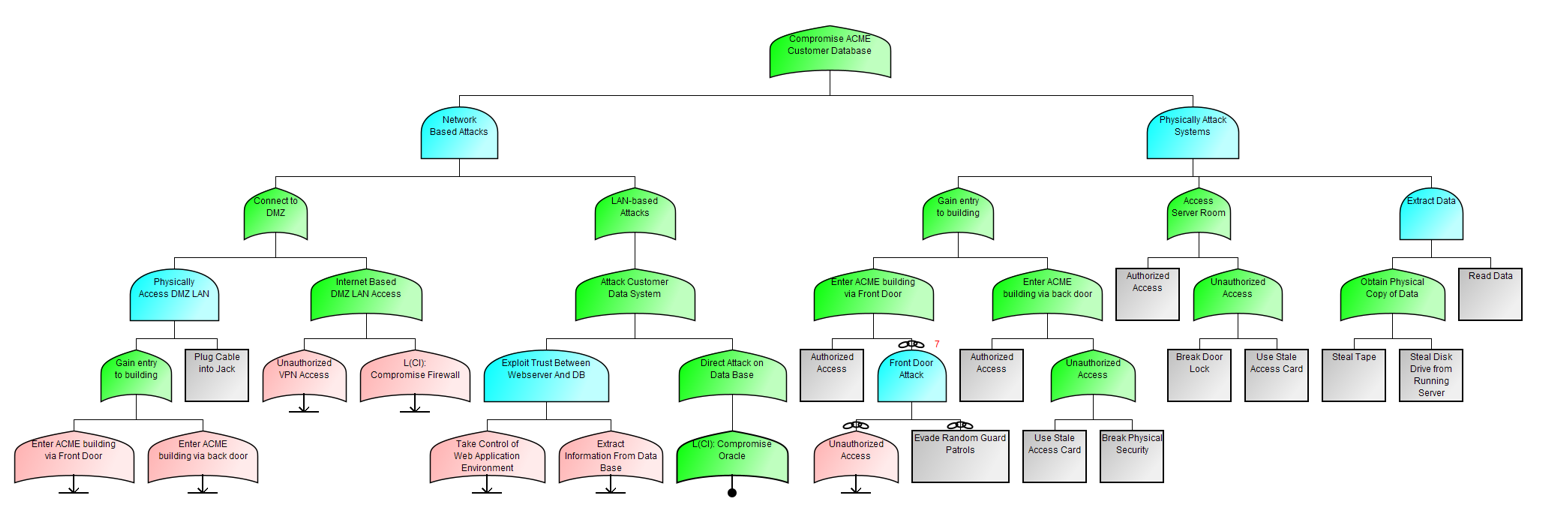
At the core of our work is SecurITree®, our proprietary attack-defense modeling platform. Through simulation and modeling SecurITree empowers you to understand how adversaries view (and will exploit) your attack surface. This provides an understanding of cyber-physical risk that is profound and leads to empowering your executive to make strategic security decisions.
Whether you choose to conduct your own assessments, or opt for Amenaza's consulting team taking the lead, SecurITree's attack tree-based simulations will predict adversarial behavior in almost any type of cyberphysical system (IT, OT, hybrid IT/OT, embedded). These outcomes easily map to regulatory frameworks such as SEC 2023 rules, OSFI's B-13, and NIS2.
- ✔ Board-ready risk prioritization
- ✔ Simulation of attacker feasibility
- ✔ GRC-aligned cyber-physical security strategy
“Amenaza gave our board clarity no other firm had delivered — turning cyber-physical risk into decisions we could act on.”
— CISO, Fortune 500 Logistics Company