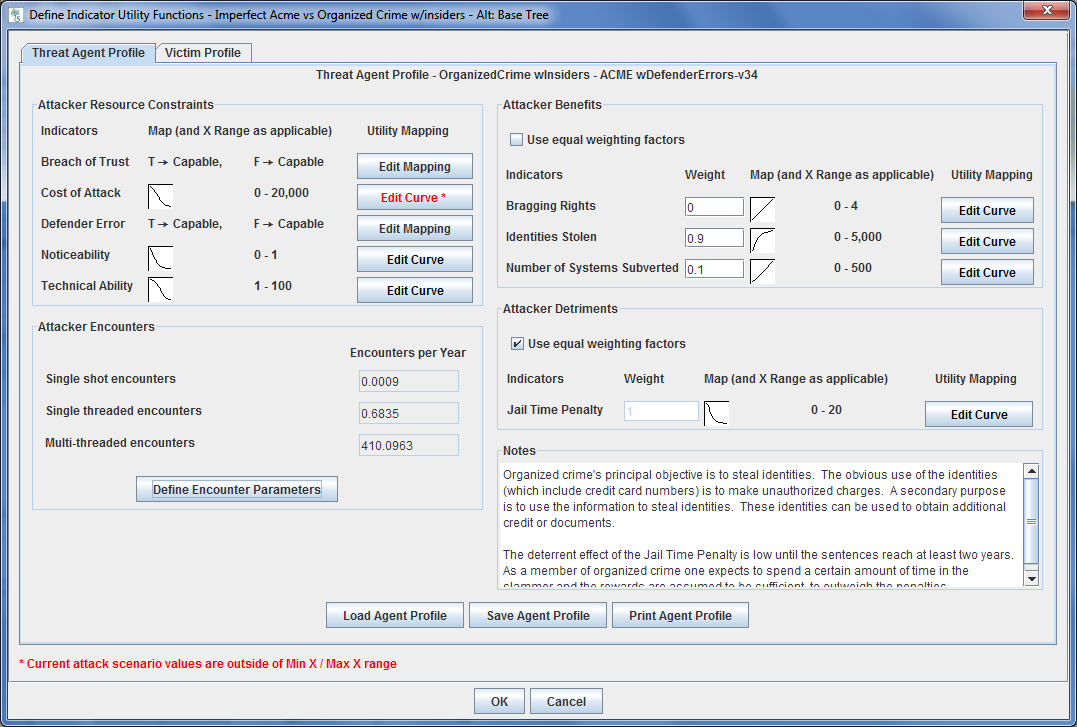
A description of an organized crime (with insiders) group operating against the hypothetical Acme company. Utility functions are used to describe the capabilities of this adversary and what goals they are trying to achieve. This input will be used to estimate the probability the adversary will perform the various attack scenarios in an attack tree.

Click to see other screenshots:
Acme Attack Tree
Copyright © 2026 Amenaza Technologies Limited. All rights reserved.